SST25VF016B programming
http://www.malinov.com/Home/sergeys-projects/spi-flash-programmer
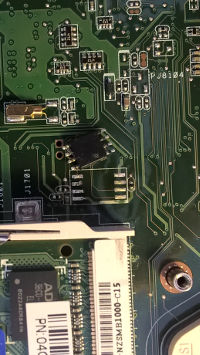
My friend contacted me for help with an Asus K52N notebook. Its user forgot the BIOS password, so the machine was bricked. We found out that the password was saved in the SST25VF016B memory chip where the BIOS code resides. After a bit of searching we found a simple SPI programmer, so we decided to clear the memory and write a new BIOS to it in order to clear the password.
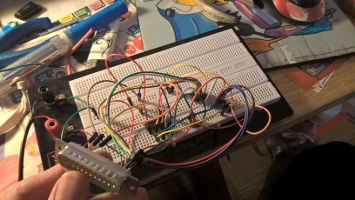
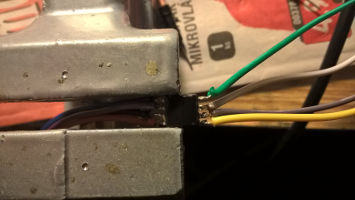
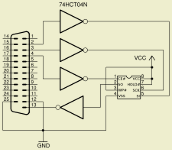
The programmer's circuit was built quickly on solderless breadboard with jump wires. Instead of CD4049UB we used 74HCT04. The problem arose when we tried to rewrite the memory. We could not verify the data successfully and it seemed that every read was giving us a different values. We didn't know if it was an error in write or read operation, but it didn't take us a long time to found out that it was caused by electrical noise. Well, look at the pictures ... you can almost see it in that tangle of wires.
We decided to modify software for the SPI programmer. Instead of writing the whole address space and then reading it back, the modified program erases, writes, and verifies the memory by 4096 byte sectors. In addition, it tries to repeat unsuccessful erase and write operations multiple times and when it succeeds, it goes for the next sector. The idea behind writing by sectors was that if one sector gets corrupted it's better not to rewrite the whole memory, because even if the corrupted sector will be successfully written, it will also erase the good ones and the probability of another sector corruption will be quite high. If a sector cannot be successfully written, the program ends. But as an argument to write operation it takes sector number to begin writing from, so we can restart the writing from the last corrupted sector. Using this technique we were able to write the memory.
Also, we added verify operation which works on the same principle and uses the same arguments as write, but it does not unlock the memory for modification (writing), so if we use this operation, we can be quite sure, that content of the memory is not corrupted.
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Processing sector 1
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Processing sector 2
...
Processing sector 373
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
ERROR: cannot write sector
$
$ ./prog write k52.213 373
Processing sector 373
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
Processing sector 374
...
Processing sector 511
Read: 0 KBytes
Read: 0 KBytes
Read: 0 KBytes
OK: memory programmed
$
ERROR: sector number 512 is outside range [0,511]
$